How to Secure Your Website with WordPress Firewalls

Remember the sky-high white wall in Game of Thrones that kept the mighty white walkers out of the seven kingdoms? Or, the Great Wall of China that was designed to protect the Chinese Empire from outside invasions?
Apparently, the stronger the wall is, the secured are the forts and castles inside it.
A WordPress firewall is that protective wall for your WordPress site. It keeps all unwanted traffic outside while only allowing access to the authorized IPs.
Think of your WordPress site as the castle in the center and your network perimeter as your entire kingdom. Now, you can put a protective wall around your kingdom or around your castle.
However, a wall around both the castle and the kingdom ensures added security. This way, if your first layer of defense (the outer wall) is breached, the inner wall holds the fort.
Read below to understand what the different layers of firewall mean for your WordPress website, what can be an ideal firewall combination for your site, and how to configure and maintain your WordPress firewall.
Let’s dive right in.
What is a WordPress firewall
A WordPress firewall is your site’s last line of defense. It’s installed directly on your WordPress installation and runs within WordPress to monitor and filter traffic and actions. This means plugin firewalls can see and analyze traffic only after the traffic has been accepted by your web server and handed to WordPress.
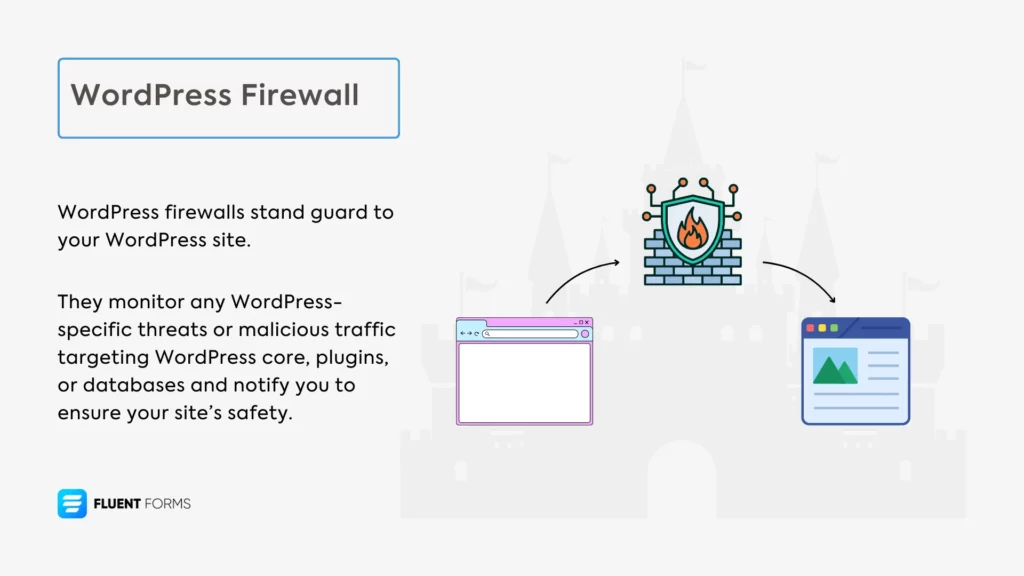
WordPress firewall plugins primarily monitor and protect at the application level. Application-level firewalls understand and monitor the behaviors, requests, and activities that are specific to a particular application (in this case, WordPress).
For WordPress, application-level protection includes:
- Monitoring WordPress-specific files and directories
- Understanding WordPress database structures and query patterns
- Recognizing attacks against WordPress admin areas
- Detecting plugin and theme vulnerabilities
- Filtering malicious content submissions
- Blocking suspicious login attempts to wp-admin
- Preventing unauthorized modifications to WordPress core files
Firewall plugins are easy to install through the WordPress admin panel, and they work on any hosting environment, including shared hosting. They don’t require any server configuration, and you can update them like any other WordPress plugin.
How WordPress firewalls work
WordPress firewall plugins are essential for your website because many attacks that target WordPress sites are designed to look like legitimate traffic at the network level. Therefore, unless your website is protected by a firewall plugin, that malicious traffic can easily harm your WordPress core, files, and databases.
This is how WordPress plugin firewalls protect your site:
WordPress security tools understand common WordPress attack patterns like plugin vulnerabilities, theme exploits, and brute force attacks against wp-login.php and can notify you in due time. They can also flag modifications to core WordPress files, unauthorized plugin installations, or suspicious admin actions.
Moreover, plugin firewalls monitor WordPress database tables for unauthorized changes and SQL injection attempts. Additionally, they understand plugin vulnerabilities and prevent exploitation of known security issues.
Furthermore, plugin firewalls detect malicious code injections in posts, pages, and comments. They pay special attention to WordPress admin login attempts and two-factor authentication specifically for WordPress accounts.
Last but not least, plugin firewalls monitor your WordPress core, theme, and plugin updates to keep your site’s health in check.
However, a WordPress firewall plugin alone isn’t reliable enough to keep your site impregnable. To keep all malicious traffic outside, you need a combination of two or more different types of firewalls, depending on your site’s size and the amount of traffic it gets.
Let’s learn about the 6 types of firewalls and how they aid in your site’s protection so you can easily decide which combination is ideal for your site.
6 types of firewalls to protect your WordPress site
Firewalls are designed to detect and filter traffic based on specific rules. They’re experts on filtering traffic within their scope. However, one type of firewall isn’t much help if the attackers target a different application that’s not within its expertise.
This is because application-based firewalls are tailored to detect breaches and vulnerabilities in the code of a certain application, and network-level firewalls have a more generalized method of filtering, which application-specific threats can easily bypass.
Thus, firewalls are mainly categorized based on where they’re placed and what type of threats they filter.
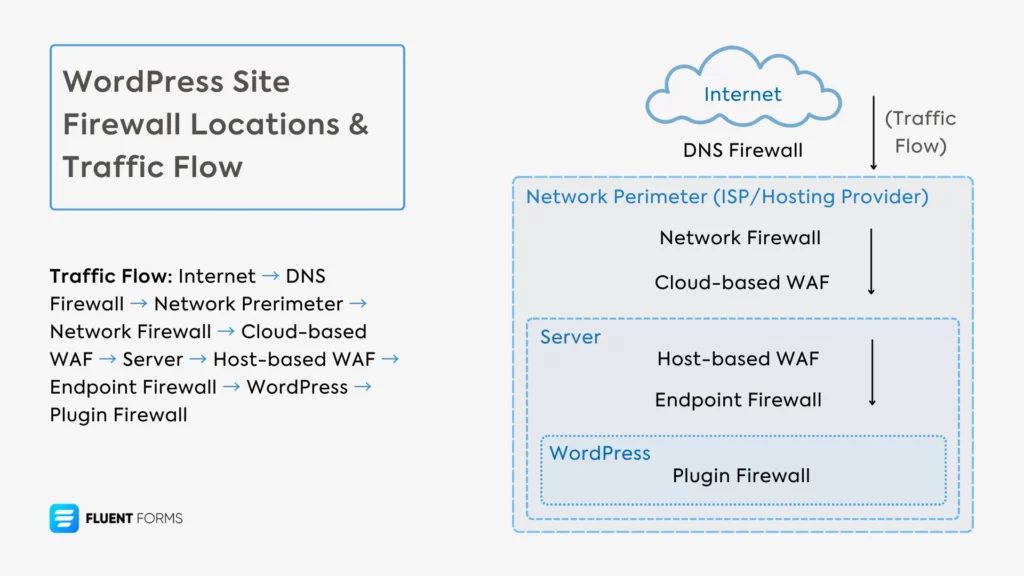
1. DNS-level firewall
DNS firewalls are your site’s first line of defense. It operates at the DNS resolution level before traffic even reaches your hosting provider. It prevents connections to known malicious domains and blocks command-and-control servers.
Examples: Cloudflare DNS filtering, Sucuri DNS-level protection, etc.
2. Network firewall
These are located at the network perimeter of your hosting provider’s infrastructure. They control traffic based on IP addresses, ports, and protocols.
So what are IP addresses, ports, and protocols?
An IP address identifies a specific device on a network (like a building’s street address), while ports identify specific applications on that device (like different apartment numbers within that building).
When data packets arrive at a device, the operating system uses the port number included in the packet header to determine which application should receive that data. This allows a single device with one IP address to run multiple network services simultaneously.
Protocols, on the other hand, are standardized rules for data transmission. The most common include TCP, UDP, IMCP, HTTP/HTTPS, FTP, etc.
A network firewall blocks unauthorized access attempts, controls which services are accessible (port filtering), prevents IP-based attacks, manages network traffic flow, performs basic rate limiting, tracks connections, etc., before traffic enters your server.
Examples: Hosting provider’s hardware firewalls, AWS Security Groups, etc.
3. Cloud-based WAF
They stand between the internet and your server, filtering malicious traffic before it reaches your hosting environment. Mostly they analyze HTTP/HTTPS traffic patterns.
Cloud-based WAFs (like Cloudflare) can absorb volumetric attacks by distributing the traffic across their global network. A volumetric attack is a type of distributed denial of service (DDoS) attack that tries to overwhelm a target website or network by consuming all available bandwidth.
They can also restrict the number of connections from a single source to help with smaller volumetric attacks. Moreover, they can scale bandwidth to automatically increase capacity during attacks.
Examples: Cloudflare WAF, Sucuri Website Firewall, etc.
4. Host-based WAF
They are installed directly on your server, examining the traffic that reaches your hosting. They can protect multiple sites on the same server and block attacks at the HTTP protocol level. However, configuring host-based WAF usually requires technical knowledge and server-level access.
Host-based WAFs have knowledge of WordPress setup. They can monitor server resources to detect unusual resource usage patterns. They can monitor file integrity and database access patterns as well. Moreover, you can setup site-specific rules on the host-based WAFs.
Examples: ModSecurity, server-level WAF rules, etc.
5. Endpoint firewall
Endpoint firewall runs on your server operating system, filtering traffic at the server level. They protect the entire server ecosystem. However, you require some technical knowledge and server-level access to configure endpoint firewalls.
They block unauthorized login attempts, prevent SQL injection attacks, protect against cross-site scripting (XSS), filter malicious traffic targeting WordPress vulnerabilities, control access to the wp-admin directory, prevent brute force login attempts, etc., before the threat reaches your WordPress site.
Examples: ConfigServer Security & Firewall (CSF), Linux iptables, etc.
6. Plugin firewall
Plugin firewalls operate within WordPress itself, acting as the last line of defense for your site. WordPress security plugins offer this solution, and they are best to protect your site against threats unique to WordPress: vulnerabilities in WordPress core, plugins, themes, database, wp-login, etc.
Examples: Wordfence, iThemes Security Pro, etc.
Choosing the right firewall combination for your site
Based on the placement and scope of each type of firewall, they can be categorized into 3 main layers.
The outer layer includes DNS firewall, network firewall, and cloud-based WAF. The middle layer consists of host based firewall and endpoint firewall. The innermost layer consists of WordPress plugin firewall. To summarize their roles:
- The outer layers (1-3) protect against large-scale attacks and known malicious sources and filters traffic before it enters your site
- The middle layers (4-5) provide server and environment protection
- The innermost layer (6) provides WordPress-specific protection
Here’s a list of recommended firewall solution combinations for websites with multiple sizes and purposes.
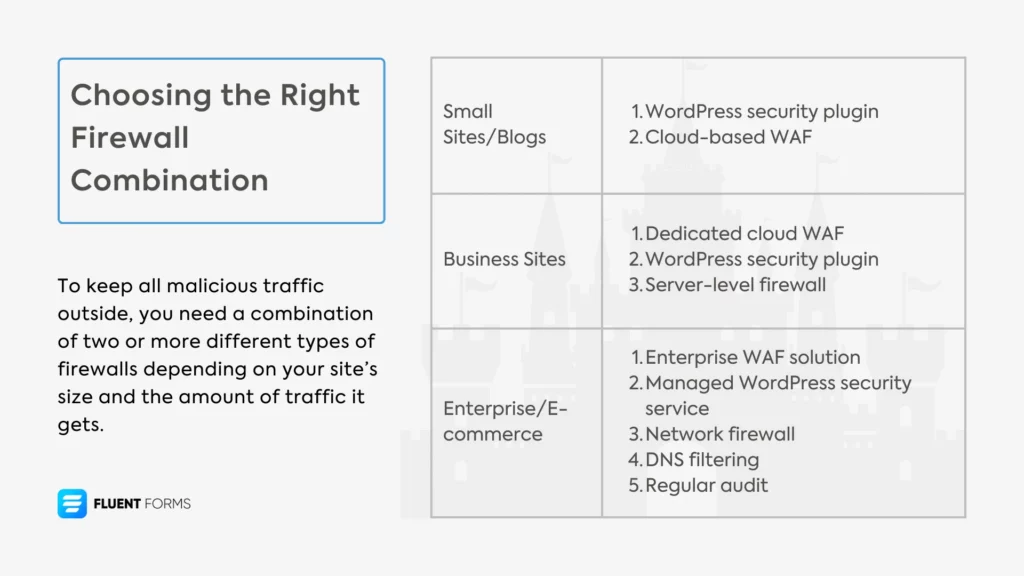
For Small Sites/Blogs:
- WordPress security plugin (like Wordfence)
- Cloud-based WAF (like Cloudflare’s free plan)
For Business Sites:
- Dedicated cloud WAF (example: Cloudflare Pro or Sucuri)
- WordPress security plugin
- Server-level firewall (if on VPS/dedicated hosting)
For Enterprise/E-commerce:
- Enterprise WAF solution (example: Cloudflare Enterprise, AWS WAF)
- Managed WordPress security service
- Network firewall
- DNS filtering
- Regular audit
The most cost-effective and complete solution for most WordPress sites would be a combination of a free and a premium solution, so it provides both network-level and application-level protection. The plugins/firewalls you choose in each case should be easy to configure and do the job well.
Configuring your firewall for maximum protection
Configuring a WordPress firewall plugin is easy. You simply upload, install, and activate it from your dashboard like any other plugin. After that, the configuration is pretty straightforward; you don’t need any technical knowledge to set it up. Follow the steps below, and you’re all set to go.
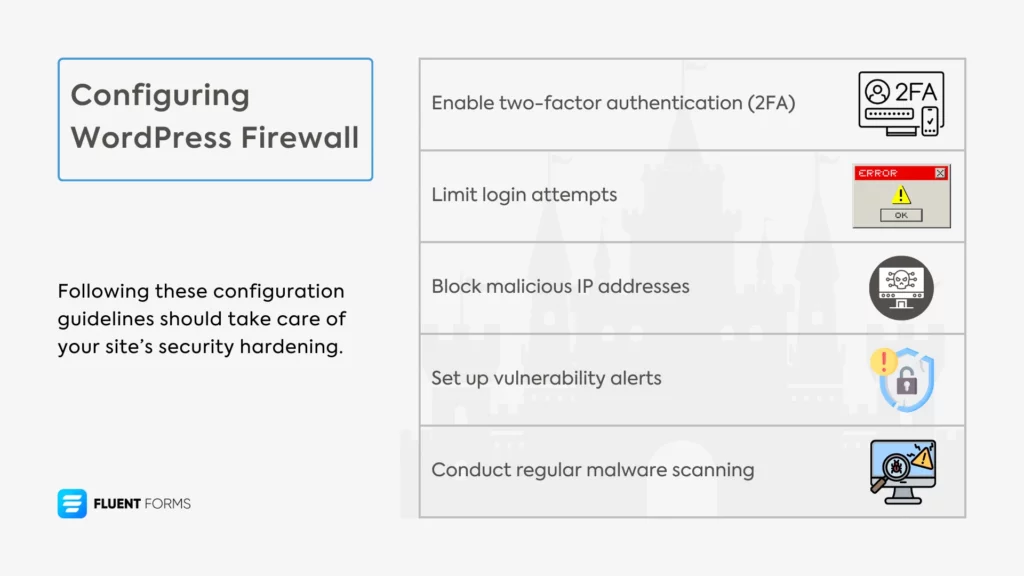
Enable two-factor authentication (2FA)
Most security plugins add a second step that requires submitting a code sent to a phone or an email. Even if a bot guesses the password, it’s stuck without that code. This cuts brute force success rates to near-zero unless they’ve hacked the 2FA as well.
Limit login attempts
You need to always limit login attempts to protect your site from brute force attacks. Bots can try thousands of ID and password combinations in a matter of seconds. Limiting login attempts slows down the attack.
Moreover, you should change the default admin username, so it becomes even harder for them to guess the combination. Moreover, don’t show hints (wrong password/username) in case of a failed login attempt to avoid accidentally helping the attackers.
Block malicious IP addresses
Blocking suspicious IP addresses and countries/regions is one of the basic settings. Doing this decreases load on your site and prevents your site from volumetric attacks.
Vulnerability alerts
Set up vulnerability alerts to be notified of potential security issues. Once you get a notification, you can review and resolve the issue before it turns into a mess.
Malware scanning
Enable malware scanning to regularly check for malicious files and code. Regular scanning makes it highly unlikely for an attack to succeed.
Following these guidelines should take care of your site’s security hardening. Pair these settings with the following best practices to ensure continued security and protection for your WordPress website.
Monitoring and maintaining your firewall: best practices
Once you set up your firewall plugin, there are still some areas that you need to revisit from time to time for optimum results.
Review firewall logs regularly
Your firewall logs contain valuable information about blocked IPs, attempted attacks, and suspicious activities. Regularly reviewing these logs offers you insight into your site’s potential security vulnerabilities and attack patterns.
You can use this insight to resolve red flags pinned by your firewall plugin, because from regular review you’ll know which alert is harmless and which needs immediate attention.
Stay informed on new threats
Cybercriminals are constantly refining their methods. They’re trying to fight the security measures in place, so they have to constantly find loopholes even in the finest firewalls. Firewall plugins know this, and they’re constantly evolving their methods to stay on top of the attackers.
So where are you on this? Even though your security solution is taking care of your site’s vulnerabilities, it’s always better that you stay in the know as to which new threats are appearing. This way, when your plugin notifies you of such a threat, you can have a look before dismissing it. This will definitely save your site in the process.
Regular security audits
You need to regularly conduct security audits of your site. The audit frequency should depend on your site’s size and purpose. An ideal period for this would be once a week.
With many security tools, you can schedule a daily, weekly, or monthly audit to save time. Security audits are like your site’s health checkup. It’s always in your best interest to make sure your site’s health is intact.
Firewall update
Choose a firewall plugin that gets regular updates. Outdated security tools are no use to you because they might contain vulnerable code. Moreover, they’re not compatible with the newest threats attackers come up with. They’re not compatible with your latest version of WordPress, themes, or plugins as well. Therefore, it’s important to update your firewall plugin at least once every 90 days.
Firewall fine-tuning
Although setting up your WordPress firewall plugin is very easy, there are some post-setup fine-tunings that you need to take care of.
This might include geo-blocking (if you own a local business, blocking foreign traffic decreases the load on your site), malicious or suspicious IP blocking, enabling other security settings that are in your site’s best interest, etc.
Additionally, you might want to revisit these settings every now and then to review if there’s any new rule that you need to apply based on how attackers modify their methods.
Regularly monitoring your firewall’s performance and reviewing the settings will ensure that your site’s health is never put at risk.
Your security tools are constantly improving and strengthening their strategy to stay ahead of the attackers. This makes your job really easy; all you have to do is make a few tweaks in the settings to match your site’s needs.
However, in case of any confusion, you can always contact a professional or your security plugin’s support team.
What’s next
If your site isn’t secured, then all the trouble of making it look great and offering an awesome user experience is pointless.
Why?
It puts your and your users’ data at risk. And that’s no picnic, especially if you handle sensitive information like passwords, credit card credentials, etc.
That’s why you need a WordPress firewall to guard your site. It filters all malicious traffic and keeps your site from harm’s way. Choose the right firewall combination suited to your site, and apply the best practices mentioned here to configure and monitor it for an optimum result.
Let us know if you have any confusion, and share your firewall tips in the comments!








Leave a Reply