12 WordPress Security Vulnerabilities and How to Prevent Them

Compare your WordPress website to your house.
It’s your online address that people can visit on the internet to get an overview of you or your business. It stores your property (content) and sensitive information. It’s also where your users come to communicate with you via chats and contact forms.
And just like your house, you need to watch its security. Otherwise, hackers might find weak spots and use them to enter your site and assume control.
Those weak spots are the WordPress security vulnerabilities, which might allow an attacker to steal your data, spy on you, lock you out, make your site the home ground of illegal activities, or even harass your visitors.
To keep your site safe, you need secure locks (passwords), regular maintenance (updates), careful choices about who has keys (admin users), and preferably an alarm system (security plugin).
Let’s see what the different WordPress security vulnerabilities are, how they can affect your site, and how you can protect your site against each of them.
What is a WordPress security vulnerability
A WordPress security vulnerability is a weakness in the WordPress core, themes, plugins, or configurations that attackers can exploit to gain unauthorized access, steal data, inject malicious code, swap content with spam links to shady sites, display unwanted ads, use server resources, spy on different accounts, etc.
Common WordPress security vulnerabilities include outdated WordPress core, themes, and plugins; weak passwords; lack of 2FA; unused themes and plugins; unnecessary admin accounts; lack of SSL/TLS certificate; insecure forms; malware; brute force attacks; SQL injections; DDoS attacks; etc.
Let’s see what these vulnerabilities mean for your site, how attackers can abuse them, and how to protect your site easily against these security threats.
12 crucial WordPress security vulnerabilities and solutions
Read below to understand how different vulnerabilities weaken your site, what type of mess they can cause if violated, and how to patch those vulnerabilities so they can no longer be taken advantage of.
1. Brute force attacks
Say you forgot where you wrote down the combination to your safe. One way of opening that safe would be to try different password combinations, like 0000, 0001, 0002, all the way to 9999, until one works. The stronger and longer the code, the harder it’s going to be to try all the combinations.
This is also one of the techniques that hackers use to break into your site. Instead of trying manually, they get bots to do it.
The bots guess random password and username combinations to gain unauthorized access, and they can try hundreds of combinations every second. This method is known as a brute force attack.
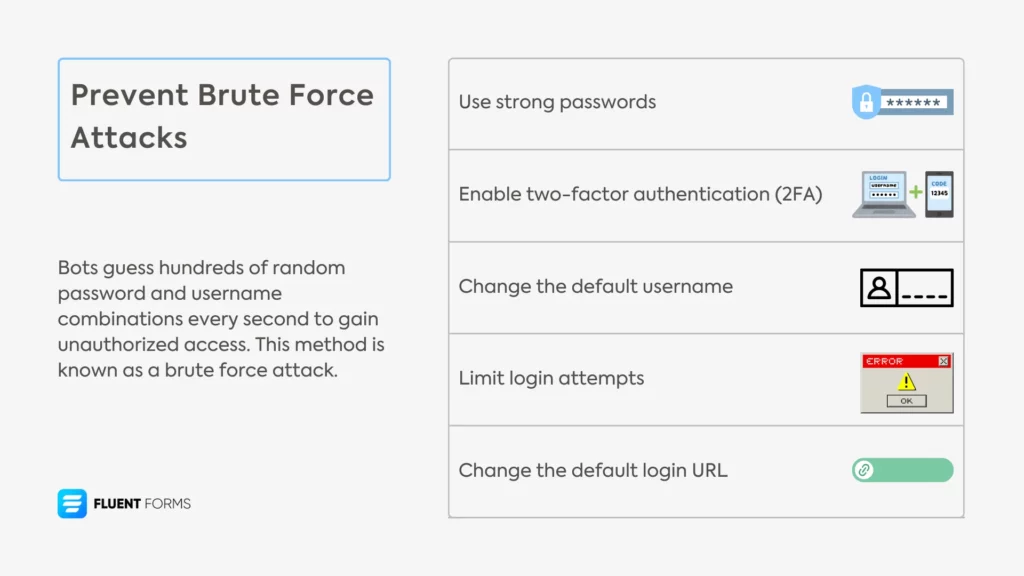
Brute force attacks are especially successful when you use weak passwords like password123 or your birthday. Let’s see how to protect your site from these types of attacks easily:
- Use strong passwords: Stronger passwords are harder to break into. Therefore, you should at least make it 12-16 characters long. Use a combination of uppercase (A-Z) and lowercase (a-z) letters, digits (0-9), and special characters (@, %, &, etc.). Don’t reuse the same password across multiple accounts.
- Enable two-factor authentication (2FA): Two-factor authentication (2FA) adds an extra layer of security. Once you correctly type in the username and password, an OTP (one-time password) is sent to your email/device. You need to type in the OTP in a very short time window (30-60 seconds) to log in. Without this OTP, hackers can’t access your site even after guessing the password correctly.
- Change the default username: A brute force attack involves guessing the login credentials correctly. Keeping the default “admin” username makes it easier since the attackers only need the password to hack into your site. That’s why you need to choose a unique username when creating your WordPress admin account.
However, if you’re an old user and kept the default username, you should replace it with a unique username. For that, create a new user account with an administrator role and then delete the former admin account with the default username. Make sure to attribute all content to the new admin user, or all your content will be deleted. - Limit login attempts: Limiting the number of login attempts slows down bots. Usually, bots can try thousands of passwords every minute. However, limiting the number of login attempts to 5 locks them out for 20 minutes after each 5 tries. In fact, you can set the lockout duration to 24 hours after a few 20-minute lockouts.
- Change the default login URL: The default WordPress login URL (wp-admin or wp-login.php) is a common target. Use plugins like WPS Hide Login to customize the login URL. Avoid predictable custom URLs like /login or /admin.
Following these steps makes a brute force attack on your site nearly impossible, as well as strengthens your site’s security. Implement them now so you don’t have to go through the hassle of a data breach or unauthorized access.
2. Outdated Software
When security problems are found in WordPress, themes, or plugins, the developers fix those and release updates. However, once those fixes are made public, hackers know exactly where the weak spots are in the old versions. Then they use tools that automatically search for websites using that outdated software and break in using those vulnerabilities. Here’s how you can easily avoid this oversight:
- Keep your WordPress core, themes, and plugins updated. Enable automatic updates for minor updates and manually update when there’s a major update available. Test updates on your staging site before applying them to your main site.
- Check for updates regularly and subscribe to relevant newsletters to stay informed.
- Only use trusted plugins and themes that receive regular updates.
- Remove inactive WordPress themes and plugins.
Following these steps keeps attackers from hacking into your site using vulnerabilities in outdated software. Remember to make backups and secure them before updating any software, so you’re covered in case anything goes wrong with the update.
3. Malware
Malware (short for malicious software) is a piece of code or program designed to gain unauthorized access, steal data, damage systems, lock files, spy on users, etc. Hackers might sneak it in through software vulnerabilities, weak passwords, etc.
Malware is categorized into different types based on how it operates. For example, viruses need manual activation (like clicking a link), while worms can self-replicate; trojans disguise themselves as useful software but open a backdoor for attackers once installed; ransomware locks victims’ files and demands payment; spyware secretly monitors and collects user information (like browsing habits, login credentials, etc.); adware shows unwanted advertisements to users, etc.
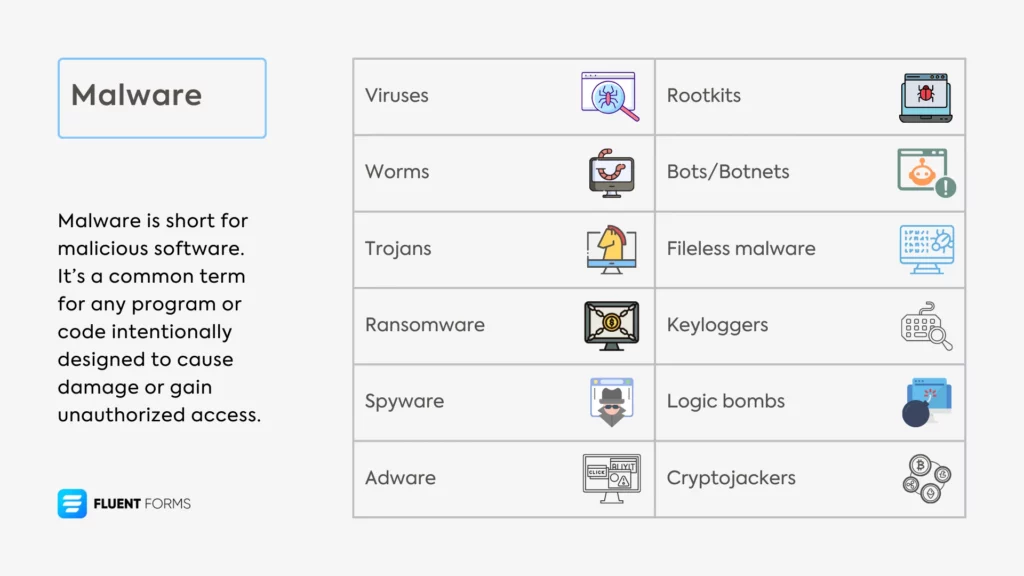
Here’s how you can protect your site from malware:
- Don’t click suspicious links or download from untrusted sites
- Keep your software updated since updates patch security vulnerabilities
- Use a reputable and trustworthy security plugin
- Regularly back up your files and databases, and store them on a separate server (you’ll need it for post-malware recovery)
In case you notice common signs like redirects to unfamiliar sites, pop-ups, slow performance, reports of odd behavior from visitors, strange login attempts, etc., you need to locate and remove the malware as soon as possible.
4. Structured Query Language (SQL) Injections
SQL (Structured Query Language) is used to talk to databases. Hackers use SQL injection to mess with a website’s database by slipping harmful instructions into input fields (like forms, URL parameters, or search bars). If the website isn’t equipped or configured to catch these tricks, the hacker can steal data or even take over the site.
For example, a library’s website has a search bar where you can type in a book’s title, an author’s name, etc. The software then processes your request and checks the library’s database for the book’s availability. A hacker might inject SQL using this search bar to request the library’s secret files, like user passwords.
SQL injections can cause data theft (extracting sensitive information like usernames, passwords, or emails), data manipulation (modifying or deleting database records, like changing admin passwords), user role alteration to gain admin access, etc. Follow the preventive measures below to protect your site from SQL injections:
- Use prepared statements for database queries to sanitize inputs. This way, the database treats any input as just data (instead of as commands). So even if someone types SQL commands, the database sees it as regular text.
- Regularly update WordPress core, themes, and plugins to patch vulnerabilities
- Remove unused plugins/themes
- Validate input types (for example, ensure numeric fields only accept numbers)
- Install a trusted security plugin
- Protect your site with a Web Application Firewall (WAF)
These tips will help you maintain your database integrity and keep your site safe by minimizing the chances of an SQL injection. However, it’s best to keep regular backups as a safety net.
5. Cross-Site Scripting (XSS)
Attackers often inject malicious scripts (usually JavaScript) into web pages, known as cross-site scripting (XSS). When other viewers visit that page, the code runs in their browser and might steal data, impersonate them, redirect them to phishing sites, etc., even without them clicking anything.
WordPress sites are vulnerable to XSS if themes, plugins, or custom code fail to sanitize user input. Common XSS entry points include comment forms, search fields, contact or user registration forms, URL parameters, etc. Here’s how to keep your website safe from XSS attacks:
- Use WordPress’s built-in sanitization and escaping functions to clean inputs and outputs
- Implement a CSP (content security policy) header to block unauthorized scripts from running on your site.
- Use a security plugin and a web application firewall.
- Keep your software updated and only use trusted themes/plugins
- Validate user input on the server side as well as the client side
XSS attacks can compromise user data, damage your site’s credibility, and lead to legal or financial consequences. Follow these best practices to protect your users and earn trust.
6. Cross-Site Request Forgery (CSRF)
What if a scammer mails a letter to your HR with your return address on it that says, “Please send my paycheck to this new address”? If the company doesn’t verify it’s from you, the scammer is likely to win.
The same thing happens with a cross-site request forgery (CSRF). When users visit a compromised site while still logged in, hidden code in that compromised site sends commands to your site. Without proper security measures, your site thinks those commands are from the legitimate user and therefore executes them. Hackers exploit the user’s session/login cookie to trick your website into this.
A CSRF attack might enable intruders to modify user settings, post content, delete or steal data, lock out legitimate users, etc. Here’s how you can prevent CSRF in WordPress:
- Implement custom anti-CSRF tokens for sensitive actions. Generate a unique token per session and include it in forms or AJAX requests. It’s like a secret password that changes every time users load a page. The sketchy site doesn’t know this password, so its fake requests get rejected.
- Make users re-enter their password for critical actions, like changing email or deleting content.
- Set the “SameSite” attribute on session cookies to prevent them from being sent with cross-site requests.
- Check the HTTP “Referer” header to ensure requests originate from your site.
- WordPress provides nonces (numbers used once) to verify the authenticity of requests. Add a nonce to forms and validate it on the server.
- Keep your software updated and use a trusted security plugin.
Following these steps will save you and your users from the consequences of a CSRF attack.
7. Unauthorized Admins
Unauthorized admins refer to illegally created accounts with administrative privileges (modifying site content, installing plugins, changing settings, accessing sensitive data, etc.). Unauthorized admins often result from security vulnerabilities in outdated software, social engineering, credential theft, insecure hosting, etc.
Hackers can compromise your content, themes, plugins, and sensitive user data; inject spam links; install backdoors, etc., through admin access. You can easily avoid this catastrophe by:
- Using strong and unique passwords and enabling 2FA.
- Assigning admin roles only to essential users. Use lower-privilege roles (like editor, author) for others.
- Regularly monitoring user activity and looking into anything suspicious.
- Limiting login attempts
- Keeping your software updated
- Investing in a good hosting provider and security plugin
- Implementing firewalls
Always have a few (3-5) recent versions of backups ready. You can use them to recover your site immediately in case you notice suspicious activities. Remember to test backups on a staging site first before using them.
8. Weak Passwords & lack of 2FA
Intruders use techniques like brute force attacks or dictionary attacks to break into weak passwords. Brute force attacks involve trying every possible password combination, while dictionary attacks use a very large set of words and phrases to generate potential passwords. Both of these attacks are conducted by bots. Bots are relentless and can attempt thousands of passwords every minute. Thus, breaking into a weak password is like child’s play for them.
2FA (two-factor authentication) adds an extra layer of security to logins. After typing in the correct username and password, an OTP (one-time password) is sent to the user’s device/email. If 2FA is enabled, guessing the correct password is useless to attackers unless they can access the OTP as well. Thus, the lack of 2FA makes breaking into your site almost twice as easy.
Here’s what you should do:
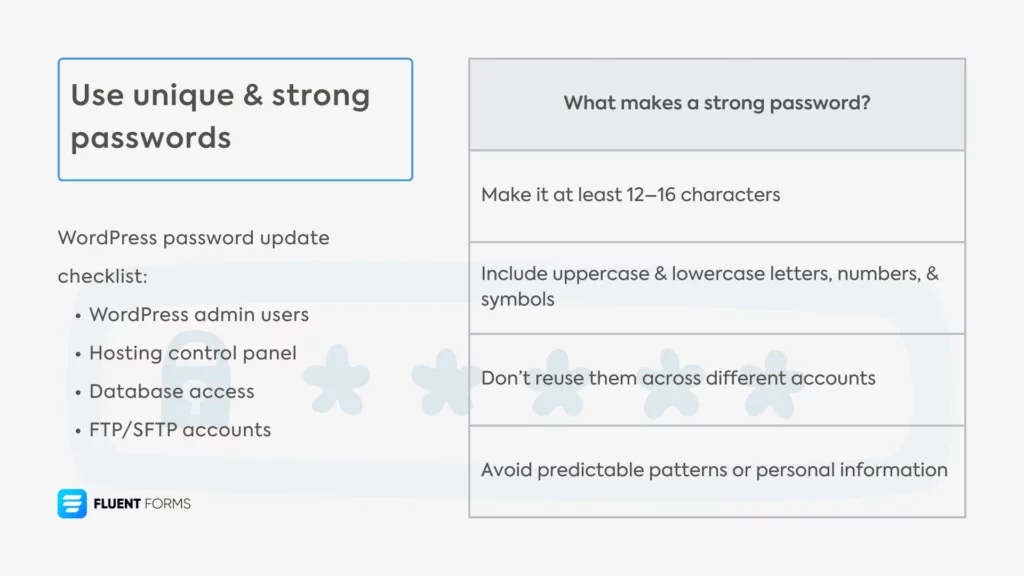
- Make your passwords long (at least 12-16 characters)
- Include uppercase and lowercase letters, digits, and special characters
- Make sure there’s no recognizable pattern in your password
- Use a unique password for each account (like WordPress admin users, hosting control panel, database access, FTP/SFTP accounts, etc.).
- Activate 2FA from your security plugin’s settings
Following these best practices strengthens your login security and improves your site’s overall health.
9. Distributed Denial-of-Service (DDoS) Attacks
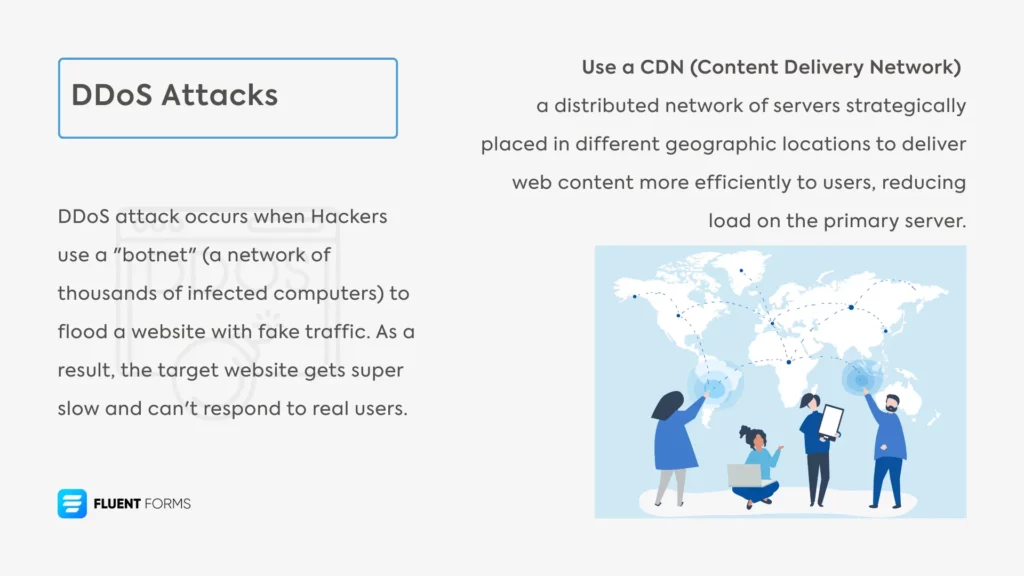
Hackers use a “botnet” (a network of thousands of infected computers that may not even know they’re infected) to flood a website with fake traffic, like tons of requests to load a page or data at once. As a result, the target website gets super slow from all the fake traffic and can’t respond to real users. This type of attack is known as a DDoS (distributed denial-of-service) attack.
DDoS attacks are usually launched to take down competitor websites, take revenge, cause distraction while doing something worse, demand ransom money, or simply cause chaos. Follow these tips to protect your site from a DDoS attack:
- Use a content delivery network (CDN). A CDN is a distributed network of servers placed in different locations that store copies of your static content so visitors can access files faster from the closest server. During a DDoS attack, a CDN helps distribute traffic across multiple servers worldwide, reducing the load on your primary server.
- Have extra servers ready to handle sudden traffic spikes.
- Use a web application firewall (WAF) to filter malicious traffic. Configure rules to block known attack signatures.
- Use DNS providers with DDoS mitigation to filter traffic before it reaches your server.
Although a DDoS attack isn’t about data theft, it still causes chaos and inconveniences your real users. Besides, without the necessary measures in place, the traffic load might even crush your servers.
10. Search Engine Optimization (SEO) spam
After sneaking into your site, hackers often add hidden texts (like stuffed keywords unrelated to your site) or spammy links. These might not be visible to you because the text color may be the same as the background color. However, search engines can see them and lower your site’s ranking. These links might also contain malware or redirect visitors to spammy sites or unwanted ads.
Let’s see how you can stop your site from being used as an attacker’s puppet.
- Keep WordPress, themes, and plugins updated
- Use strong passwords and enable 2FA
- Install a trusted security plugin
- Secure your website forms
- Regularly check your site for content you didn’t create
- Monitor your Google Search Console for warnings
SEO spam is basically digital graffiti, someone vandalizing your website to promote their stuff. If you’re not careful, it might ruin your site’s reputation or lead to Google blacklisting your site. Follow these security hardening tips to avoid that becoming a reality.
11. Insecure HTTP website
HTTP (Hypertext Transfer Protocol) is the basic way websites communicate with a user’s browser. It doesn’t encrypt the data. As a result, anyone accessing the network can also read data (for example, login credentials) like plain text that a user submits to an HTTP website and change it easily.
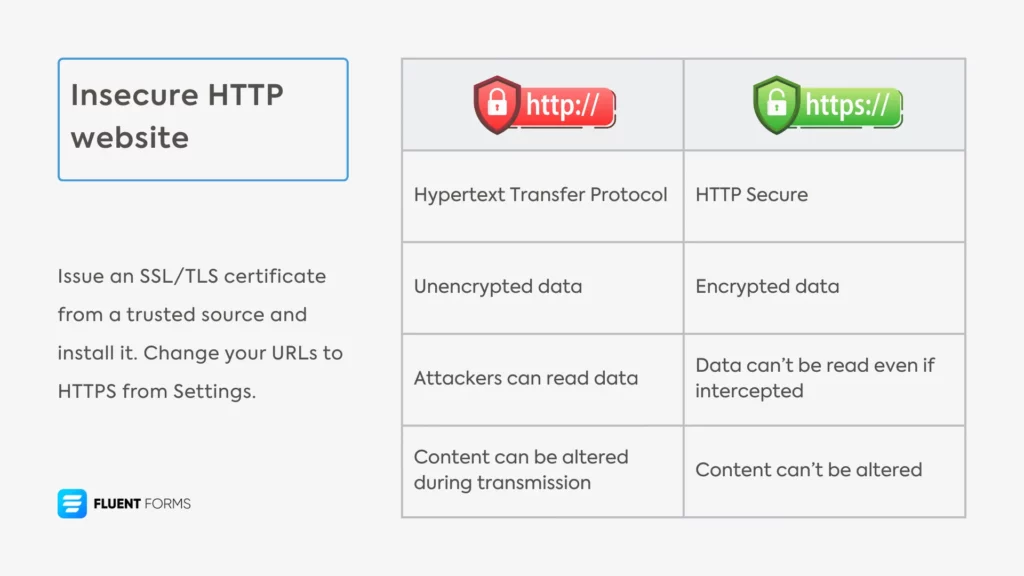
Moreover, browsers flag HTTP sites as “Not Secure,” driving users away and attracting spammers. Google lowers HTTP sites in rankings as well. To ensure data safety and SEO benefits, follow these best practices:
- Switch to HTTPS: The “S” in HTTPS stands for “secure.” An HTTPS site encrypts user data, so even if someone intercepts it, they can’t decrypt the data without the correct cipher key. Issue an SSL/TLS certificate from a trusted source and install it. Change your URLs to HTTPS from Settings, and redirect all traffic to a secure connection. Check for the padlock icon in browsers that indicates security.
- Pair strong passwords and 2FA with the SSL certificate to harden your site security further.
An HTTPS site ensures no one tampers with information in transit, resulting in user trust, SEO boost, and site credibility. Apply for an SSL certificate if you haven’t already.
12. Insecure forms
Your website has forms on multiple pages for collecting user information like email, bank credentials, address, and other personal details. Securing that information is important to earn trust and maintain data safety.
Besides, forms also contain transaction history, sales records, etc., that you don’t want your competitors to get their hands on. Moreover, attackers often use bots to post spam in different input fields, login and comment forms, etc., which might compromise your site’s credibility and your users’ safety.
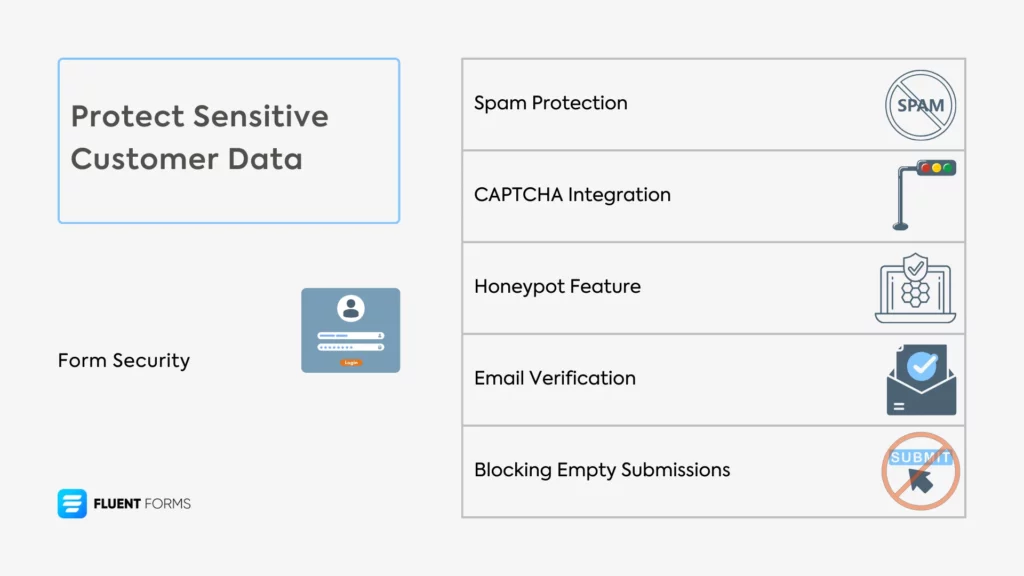
- Solution: Use a secure form plugin. Fluent Forms is the best contact solution for your site.
It comes with all kinds of form security – an SSL certificate, spam protection, CAPTCHA integration, a honeypot feature (a hidden trap for bots that humans can’t see), user login options, email verification, blocking empty submissions, file type upload restrictions, etc.
It also integrates with Akismet, CleanTalk, Turnstile, and reCAPTCHA for more targeted form security.
Secure forms are one of the most basic necessities for your website. You can’t take any risk when it’s your users’ data at stake. It can cause legal messes, reputation loss, and financial harm for you and your users. Switch to a secure form builder now to avoid facing any of those!
With the right knowledge, it’s quite easy to patch the WordPress security vulnerabilities with just a few clicks and tweaks in the security settings. However, WordPress doesn’t have an easy configuration for some of these settings. You can use FluentAuth, by the developers of WPManageNinja, to execute them without any hassle. And the best part is, this plugin is completely free.
On a final note
It’s really easy to hack a WordPress site with security vulnerabilities like outdated software, weak passwords, lack of 2FA, unlimited login attempts, untrustworthy plugins, insecure forms, lack of an SSL/TLS certificate, lack of firewalls, etc. Patch these security issues following our instructions above on a top priority basis to make your site practically impregnable.
Installing a standard security plugin covers you for all the basic WordPress security vulnerabilities. Security plugins have features to protect you against malware, brute-force logins, SQL injections, XSS attacks, DDoS attacks, and many more. They also take care of emerging new threats, scheduled audits, and backups.
Hackers are constantly coming up with new tricks, but developers are working harder to keep them at bay. That’s why hardening your site’s security isn’t a one-time thing. You need to conduct regular audits following a comprehensive security checklist.
The resources and the knowledge required to keep your site safe are always one search away. Subscribe to WordPress’s and your plugins’ newsletters for updates, new releases, and bug fixes. Leave a comment if you have any questions on WordPress security or want to share your insights!







Leave a Reply